Sandia's approach works like this: different device drivers for various wirless gear exhibit different patterns of transmission. By matching the patterns to an established database of card/driver combinations, the device driver running on some nearby machine can be identified using PASSIVE monitoring that is impossible for the target machine to detect. Encryption schemes are useless for thwarting this type of driver fingerprinting. Once a particular driver is identified, then an attacker could go to work on the particular security vulnerabilities of that driver.
I will say this -- ever since wireless came out I have been highly suspect of its ability to ever be truly secure. I don't trust it, and would never use it. My house is wired with double shielded(outer mesh, inner foil) copper cable.
Sandia National Lab(this is a PDF document)
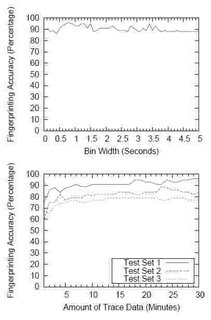
...We designed, implemented, and evaluated a technique
for passive wireless device driver fingerprinting that
exploits the fact that most IEEE 802.11a/b/g wireless
drivers have implemented different active scanning algorithms.
We evaluated our technique and demonstrated
that it is capable of accurately identifying the wireless
driver used by 802.11 wireless devices without specialized
equipment and in realistic network conditions.
Through an extensive evaluation including 17 wireless
drivers, we demonstrated that our method is effective in
fingerprinting a wide variety of wireless drivers currently
on the market...
1 comment:
The famous painter Pablo Picasso burned many of his paintings to stay warm when having financial troubles advance cash
Post a Comment